ISO 27001 License

ISO 27001 License
Information Security Management Certification Under ISO
The ISO 27000 family consists of a series of standards that pertain to information security. Evolution of ISO/IEC 27000 family
In 1995 the British Standards Institution (BSI) introduced the BS 7799 for secure Information technology standards. In 2000 the same was replaced by the ISO/IEC 17799 which was further revised in 2005. The next revision was published in 2013 as ISO/IEC 27000:2013. The latest revision, however, happened in February 2018 and is called the ISO/IEC 27000:2018.
These standards ISO/IEC 27000 that pertain to Information technology security techniques and requirements for setting up a full-proof Information security management system has been the brainchild of the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
Objective of ISO/IEC 27001 Certification

The basic purpose of this family of standards is to establish and implement an information security management system that is able to keep sensitive information and data secure by proper application of risk management processes. It lays down rules and requirements for managing people, IT processes and systems and keeps on continually improving them with the objective of securing information and instilling confidence in its internal and external stakeholders including customers. This family of standards not only meant for big business houses, but it also applies equally to smaller and medium scale businesses too. Any organization that adopts the ISO/IEC 27000 family of standards is able to manage their financial information, intellectual property, details of employees or any other information of third parties safely and securely.
Benefits of ISO/IEC 27001 Certification

Protection of data privacy and exchange of sensitive information in a secure manner
Minimizing chances of being exposed to risks thereby saving precious time and money
Helps in creating a clear and precise security structure for the business
Helps build brand equity as customers and stakeholders view the organization favorably
Helps in compliance with legal obligations
Creates a competitive advantage thereby leading to new business opportunities
The organization is better prepared to deal with growing menace of cyber crimes.
Though the certification is not done by the International Organisation for Standardization, most of the organizations get the certification done to benefit from international best practices while others get certified to instill confidence in customers, clients, and other stakeholders.
Registration process of ISO/IEC 27001
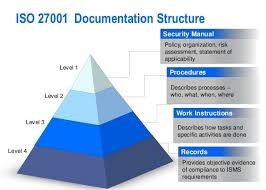
The certificate is awarded by a third party accredited certification body after it carries out a formal audit of the company’s ISMS. This certificate has a validity period of three years post which the company needs to reapply for recertification. During this period, the organization needs to ensure that it undertakes all necessary steps to maintain the certification and keep its ISMS compliant and continually improving as per ISO/IEC 27001. Surveillance audits will be carried out by the certifying body at least once a year in which only a part of the complete ISMS will be verified and reviewed. It is only at the end of the three-year term, that the external body will audit the entire ISMS to check conformance.
Task 1: first step in to identify the need as well as garner top management’s support to bring into place an information security improvement program.
Task 2: draw up a comparison between the existing IT security system and the requirements mentioned as per ISO/IEC 270001. It is also essential to understand the departments and business units that are required to be covered as part of implementing the changed system.
Task 3: carry out a detailed risk assessment
Task 4: draw up a plan to treat this risk by allocation resources, responsibilities, and appropriate actions.
Task 5: prepare a Statement of Applicability and mention the applicable controls required for the ISMS and the process of implementing the same.
Task 6: create a detailed project for implementing the identified controls.
Task 7: put the ISMS into operation. After this, it is required to conduct internal audits and management reviews.
Task 8: apply for certification.
Task 9: hiring of external certifying agency so that an external audit is carried out. Certification is done after reviewing documentation, on-site visit, and review of systems and processes.
What We Offer
Packages & Pricing
6499
Basic
10000
Standard
19999
premium
FAQs For Private Limited Company Registration
LicenseHub - Copyright 2023. All rights reserved.
- Designed By-WebsApex

